.
Prior to the invasion, Russia and some Commonwealth of Independent States (CIS) countries were typically excluded from cyberattacks or from the ransomware target list, most likely due to criminal actors residing in those countries or fearing reprisals.
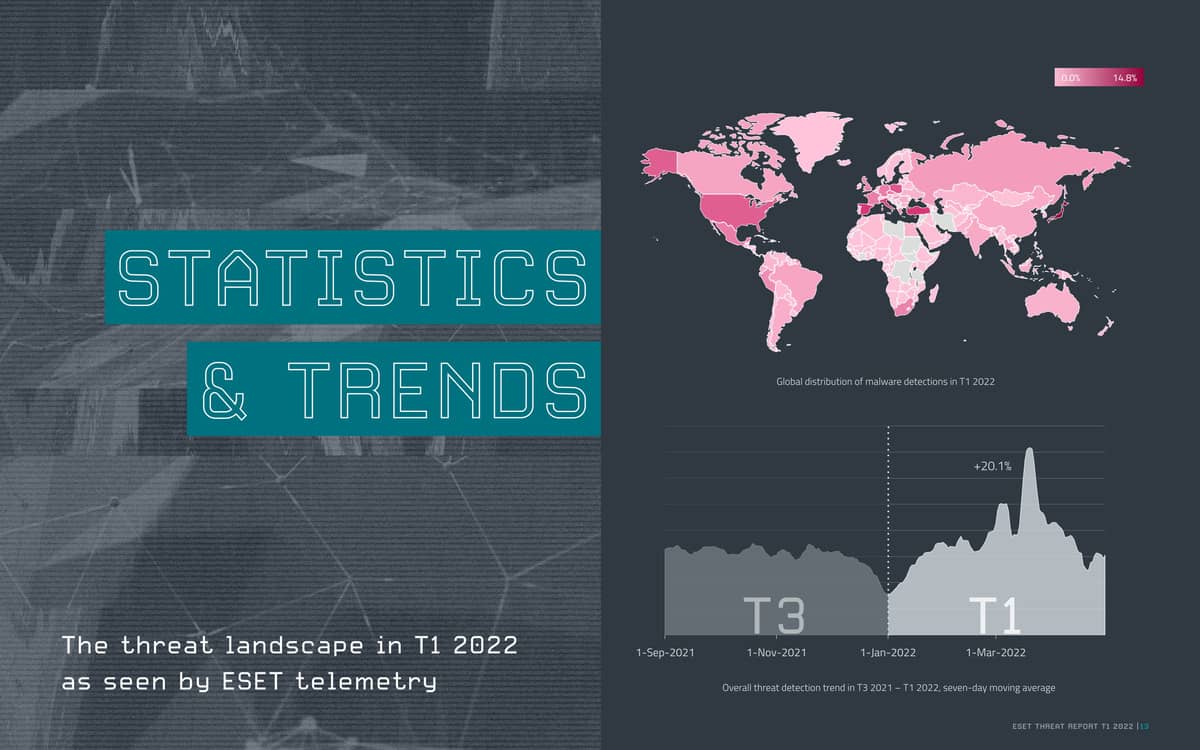
In the first quarter of 2022, for example, Russia had the highest percentage of detections (12%) in the Ransomware category.
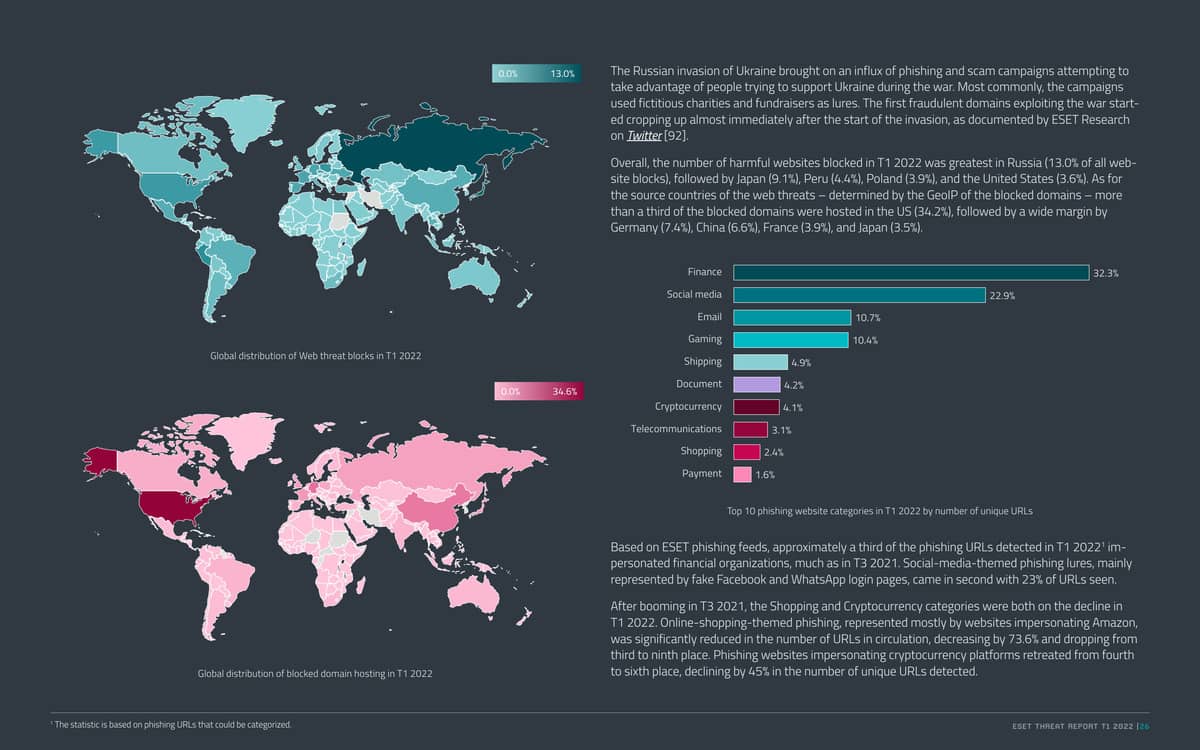
The hack resulted in a rise in phishing and other scam campaigns who try to take advantage of people looking to support Ukraine. This growth was detected shortly after the start of the invasion.
The number of cyberattacks involving a computer accessing a network without direct contact (or Remote Desktop Protocol – RDP attacks) dropped for the first time since early 2022. The reduction of remote work, as well as the disruptions and sanctions resulting from the invasion, which conditioned access and availability to infrastructure, are likely reasons that justify this decline.
Changing the landscape of cyber attacks according to ESET
ESET, a leading European company in cybersecurity solutions, today released its report for the first quarter of the year, the Threat Report T1 2022, which compiles key statistics from its detection systems, highlighting notable examples of its cybersecurity research and revealing exclusive information about current threats. As the first threat report of the current year, covering the period corresponding to the months of January to April, the Threat Report Q1 2022 also includes comments on general trends observed over these months, highlighting the main research findings.
The cyberattacks that tell the story of the war in Ukraine
The latest edition of the ESET Threat Report describes the various cyberattacks linked to the ongoing war in Ukraine that ESET investigators have analyzed or contributed to mitigating. Among them is the reappearance of Industroyer malwarewhich targeted an energy supplier in Ukraine.
Prior to Russia’s invasion of Ukraine, ESET telemetry recorded a sharp drop in cyberattacks via RDP of 41% compared to the previous quarter. The decline in these attacks comes two years after a steady rise. Among the possible reasons behind this decline, ESET highlights the drop in remote work related to the pandemic, the greater awareness among IT departments, and the war, whose disruption and sanctions will have influenced access and availability to the infrastructures involved in the attacks. RDP. Despite thatclose to 60% of the RDP attacks recorded in the last quarter originated in Russia.
Another side effect of the war was that Russia, typically a country immune to ransomware threats, was the biggest target for threats in this category in the last quarter (12%). ESET researchers have even detected lock-screen variants that use the Ukrainian national greeting “Slava Ukraini!” (Glory to Ukraine!). Additionally, there has been an increase in the number of ransomware and more amateur “wipers”. Its authors often assume the support of one of the sides in the struggle and position the attacks as personal revenge.
no surprises, the war has also been exploited by spam and phishing threat authors. Shortly after the invasion on February 24, scammers began preying on people seeking to support Ukraine, using fictitious charity and fundraising initiatives as bait. That same day, ESET telemetry detected a large spike in spam detections.
Cyber threat landscape beyond invasion
ESET telemetry also found other non-war threats. Among them, ESET highlights the reappearance of Emotet, a family of banking trojans distributed mainly through spam email campaigns. Emotet detections grew by more than a hundred compared to the previous quarter. However, Microsoft’s decision to disable Internet macros by default in Office programs will force Emotet operators to look for new avenues of attack.
Finally, the ESET Threat Report Q1 2022 reviews the most important research findings of the period. The ESET research team also revealed the abuse of vulnerable kernel drivers, high-impact UEFI vulnerabilitiescryptocurrency malware targeting Android and iOS devices, an as-yet unattributed campaign implementing the DazzleSpy malware on macOS, and campaigns by Mustang Panda, Donot Team, Winnti Group, and the APT TA410 group.
Follow all the technological updates on TecheNet through Google News. All the news in real time and without delays!
Other interesting articles:
.








