.
Kaspersky experts warn of new WinDealer malware capability spread by Chinese cybercriminal group LouYu. The threat manages to enter a system through a man-on-the-side attack.
This innovative advancement allows modifying network traffic in order to introduce malicious payloads. These attacks are particularly dangerous, as they do not require any interaction with the target for the attack to be successful.
Following the conclusions shared by the TeamT5, Kaspersky experts discovered a new method to spread the WinDealer malware. The threat is now able to leverage a man-on-the-side attack to read network traffic and insert new messages. Generally speaking, in a man-on-the-side attack, when an attacker sees a request for a specific resource on the network (through its interception capabilities or strategic position in the ISP network), it tries to respond to it before the legitimate server does. . If the cyber attacker wins the “race”, the target device will then use the data provided by the attacker instead of the normal data. Otherwise, attackers will keep trying until they finally manage to infect most devices.
After the attack, the target device receives a spyware application capable of collecting a large amount of information. Attackers can view and download any file stored on the device, and they can even run a word search on all documents. The LuoYu cybercriminal group typically targets foreign diplomatic organizations based in China, as well as members of the academic community and defense, logistics and telecommunications companies. WinDealer is the malware used to attack Windows devices.
Typically, the malware contains an encrypted C&C server through which the malicious actor controls the entire system. With information about this server, it is possible to block the IP address of the devices with which the malware interacts, neutralizing the threat. However, WinDealer relies on a complex IP generation algorithm to determine which device to contact. It includes a range of 48,000 IP addresses, making it nearly impossible for the operator to control even a small portion of the addresses. The only way to explain this seemingly impossible network behavior is that attackers have significant interception capabilities in this IP range and can even read network packets that do not reach any destination.
The “man-on-the-side” attack is especially harmful because it does not require any interaction with the victim for the infection to be successful: it just needs to be a device connected to the Internet. Also, there is nothing users can do to protect themselves other than forwarding traffic through another network. This can be done with a VPN, but this option is not available in some countries, such as China.
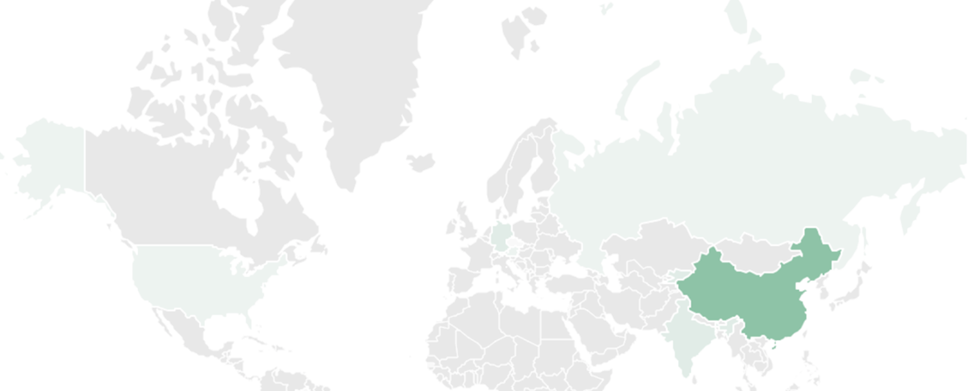
The vast majority of victims of the LuoYu cybergroup are located in China, so Kaspersky experts believe that APT LuoYu predominantly focuses on victims who speak the language and organizations related to this country. However, Kaspersky analysts also observed attacks in other parts of the world, including Austria, the Czech Republic, Germany, Russia, India and the United States.
“The LuoYo group is an extremely sophisticated threat actor. Surprise attacks are very destructive as the only necessary condition to attack a device that is connected to the Internet. Also, if you fail the first time, you can repeat as many times as you like until you succeed. This is how they manage to carry out extremely dangerous espionage attacks against their victims, who are usually diplomatic, scientific and officials from other key sectors. Regardless of how the attack was conducted, the only way for potential victims to defend themselves is to remain vigilant and rely on robust security systems that perform regular antivirus scans, network traffic analysis and an extensive log for anomaly detection.,” comments Suguru Ishimaru, senior security expert on Kaspersky’s Global Research and Analysis (GReAT) team.
To protect yourself from WinDealer malware, Kaspersky recommends:
- Robust security procedures, which include regular antivirus scans, network traffic analysis and an extensive anomaly detection log;
- Conducting a cybersecurity audit of your networks and acting in the face of any security flaw discovered in the network perimeter;
- Installation of anti-APT and EDR solutions that help detect threats, as well as investigate and resolve incidents. It is also advisable to provide the SOC team with access to the latest threat intelligence regularly updated with professional training. All these features are included in the Kaspersky Expert Security;
- In addition to properly protecting endpoints, dedicated services can help against high-profile attacks. The service Kaspersky Managed Detection and Response can help identify and stop attacks in their early stages, before the attackers achieve their objectives.
- Be aware of new threats to maintain a high level of security. O Threat Intelligence Resource Hub provides access to independent, continuously updated and global information about cyberattacks and ongoing threats at no cost to the user.
To consult the complete report on WinDealer, go to securelist.
Follow all the technological updates on TecheNet through Google News. All the news in real time and without delays!
Other interesting articles:
.









