.
Limitar a quantidade de carvão que os países podem queimar é considerado uma prioridade urgente para conter o aquecimento global. Afinal, o carvão é o mais rico em carbono de todos os combustíveis fósseis e sua combustão é o que mais contribuiu para o aquecimento planetário. Pela primeira vez em negociações internacionais, os negociadores concordaram em “reduzir gradualmente” o uso de carvão para evitar o aumento da temperatura global superior a 1,5°C no Pacto Climático de Glasgow de 2021.
A primazia do carvão nas negociações climáticas se deve em parte ao Painel Intergovernamental sobre Mudanças Climáticas (IPCC), que criou caminhos para deter o aquecimento de 1,5°C. Essas avaliações científicas priorizam a rápida eliminação da queima de carvão não apenas pela intensidade de carbono do combustível e pela necessidade de evitar o acúmulo de CO₂ na atmosfera, mas também para incentivar a disponibilidade de alternativas de custo competitivo na forma de parques solares e eólicos.
Os pesquisadores também enfatizam a importância de descarbonizar o setor de energia no início da transição verde para permitir que outros setores, como transporte e indústria, funcionem com eletricidade limpa da rede.
Isso coloca o ônus sobre certas nações de reduzir as emissões mais rapidamente do que outras. A maior parte do uso global de carvão pode ser encontrada em países emergentes e em desenvolvimento, como China e Índia. Aqui, grandes frotas de usinas e fábricas dependem do carvão, que é barato e abundante em comparação com outros combustíveis fósseis. Ao enquadrar a solução para a mudança climática como aquela em que o carvão é removido primeiro, são esses países que devem se comprometer a descarbonizar rapidamente na próxima década.

Abir Roy Barman/Shutterstock
Em nosso novo artigo, destacamos dois problemas com a maioria dos caminhos publicados para evitar mudanças climáticas catastróficas. Em primeiro lugar, é improvável que os países dependentes do carvão consigam abandonar o combustível tão rapidamente quanto esses caminhos estabelecidos.
E em segundo lugar, como este é o caso, outros combustíveis fósseis, nomeadamente petróleo e gás, devem ser eliminados mais rapidamente para compensar a saída mais lenta do carvão. Isso transferiria a responsabilidade de mitigar as mudanças climáticas para os países desenvolvidos.
O limite de velocidade na eliminação gradual do carvão
Comparamos quanto o uso de carvão deve cair nos caminhos modelados para 1,5°C com as transições de energia mais rápidas que ocorreram nos últimos 50 anos, com todos os combustíveis e em todos os países.
Essas transições são mostradas na figura abaixo e refletem uma série de motivadores, como respostas políticas à crise do preço do petróleo dos anos 1970 e eventos políticos como guerras, sanções e o colapso da União Soviética. A linha vermelha rotulada como “recorde mundial” indica o ritmo mais rápido que poderia ser viável com a vontade política de promulgar políticas ambiciosas.
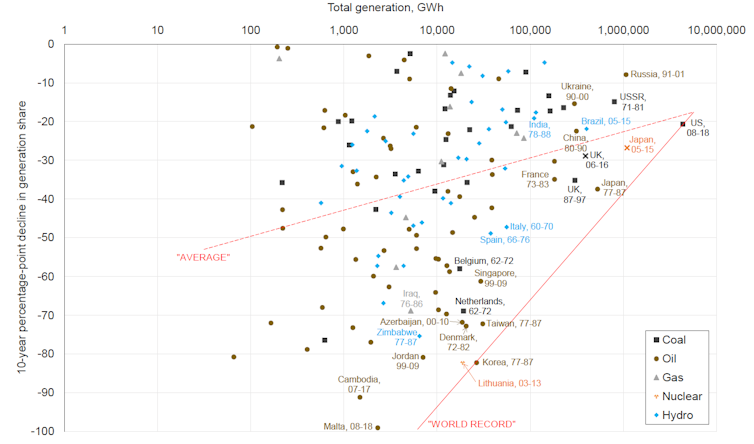
Muttitt et al. (2023)/Natureza, Autor fornecido
Com base nos caminhos modelados do IPCC, estimamos que a energia a carvão terá que ser eliminada na Índia, China e África do Sul mais de duas vezes mais rápido do que qualquer transição histórica de energia para sistemas elétricos de tamanho comparável. É improvável que isso seja alcançável ou aceitável em qualquer grande país em desenvolvimento dependente de carvão.
Um caminho mais viável para a eliminação do carvão pode usar as metas estabelecidas pela Powering Past Coal Alliance (PPCA), uma coalizão internacional de países estabelecida em 2017. A PPCA favorece um cronograma diferenciado para sair da energia do carvão, com os países ricos entrando primeiro em 2030 e no resto do mundo até 2050.
Essas metas refletem como os países em desenvolvimento são mais dependentes do carvão e têm menos dinheiro para investir na transição verde, mas carregam menos responsabilidade histórica por causar mudanças climáticas.
Esse ritmo diferenciado colocaria diversos países, inclusive a China, no limite de velocidade das transições históricas. Em outras palavras, ofereceria a eles um caminho para a descarbonização difícil, mas possível. Essa trajetória veria os países desenvolvidos reduzindo as emissões de carbono cerca de 50% mais rápido em comparação com caminhos sem a distribuição mais justa de esforços proposta pelo PPCA.
Isso inverte a narrativa das sucessivas cúpulas do clima: os países desenvolvidos, não os em desenvolvimento, são os que devem fazer mais no curto prazo para limitar o aquecimento.

Cal F/Shutterstock
Também tem consequências importantes para o petróleo e o gás. Em todos os países, a produção de petróleo e gás deve cair até 1,5°C, mesmo nas trajetórias publicadas, em vez de aumentar como a maioria dos países planeja.
Mas quando o mundo eliminar gradualmente o carvão no ritmo PPCA, o petróleo e o gás deverão ser eliminados de forma correspondentemente mais rápida. Isso tem um impacto diferente em diferentes países. Por exemplo, a produção cumulativa de petróleo dos EUA de 2020 a 2050 é 20% menor do que em uma trajetória de 1,5°C sem os esforços diferenciados propostos pelo PPCA.
Limitar a mudança climática requer a eliminação gradual de todos os três combustíveis fósseis: carvão, petróleo e gás. Nossa pesquisa revela que os modelos climáticos e os debates políticos dependem demais da redução do carvão, especialmente nos países em desenvolvimento dependentes do carvão.
Em vez disso, é necessário um equilíbrio mais justo e realista dos esforços de mitigação, o que significa mais ênfase na eliminação de petróleo e gás. Também significa maior esforço do norte global, mesmo enquanto todos os países, incluindo os do sul global, acabem com a energia do carvão o mais rápido possível.
.









